Category Archives for AWS Solutions Architect
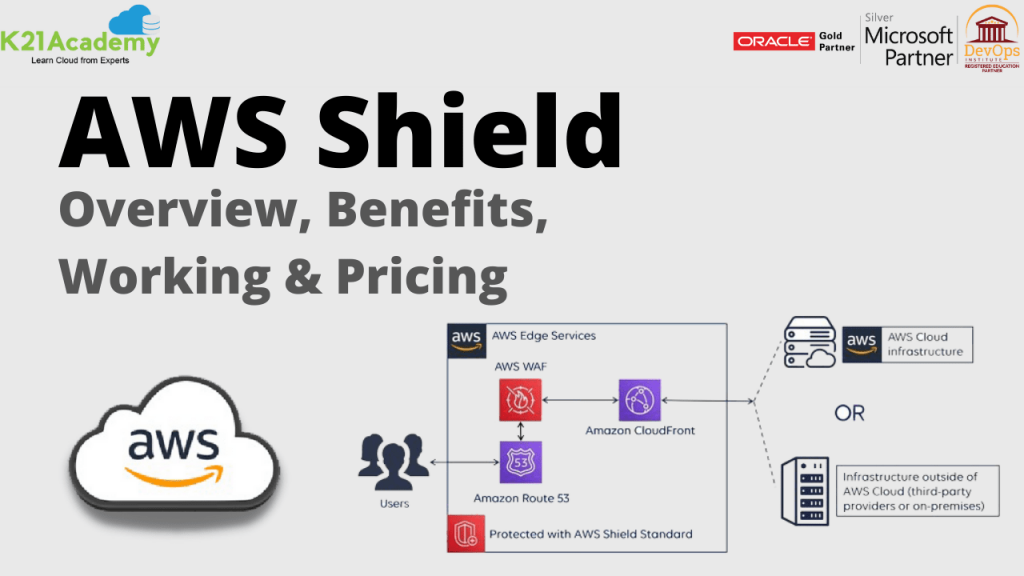
AWS Shield: Overview, Benefits, Working, Types, Pricing
✅ Protection against Distributed Denial of Service (DDoS) attacks is primarily essential for your internet-facing applications. ✅ AWS is dedicated to providing you with the tools, best practices, and services you need to ensure high availability, security, and resiliency in your defense against bad actors on the internet.🖥️ ✅ AWS Shield is a managed Distributed […]
Read More
AWS Config: Overview, Benefits, and How to Get Started?
✅ AWS Config is a service that enables you to assess, audit, and evaluate the configurations of your AWS resources. ✅ Config continuously monitors and records your AWS resource configurations and allows you to automate the evaluation of recorded configurations against desired configurations.🖥️ ✅ Benefits of AWS Config: • Config also enables you to […]
Read More
Introduction to AWS Systems Manager
AWS Systems Manager is a management service that helps to view and control AWS Infrastructure. Why AWS Systems Manager? ➪ It helps to maintain security and compliance by scanning the managed nodes and reporting on any detected policy violations. Also, it supports Amazon EC2 instances, Virtual Machines, edge devices and on-premises servers. And, in operating […]
Read More
Introduction to AWS CloudHSM
AWS CloudHSM is a cloud-hosted Hardware Security Module (HSM) service that allows you to perform cryptographic operations and host encryption keys Why AWS CloudHSM? ➪ Cloud stores all our data and applications in it. And, it may also contain some most confidential information that needs to be encrypted and stored safely in the cloud. That’s why AWS […]
Read More
AWS Shared Responsibility Model
Shared Responsibility is a collaboration or division of tasks between two or more person or bodies performing the similar activities with one goal What is Shared Responsibility Model? ➪ The Shared Responsibility Model is a cloud security framework that mandates the security obligations of cloud service providers and users to ensure accountability. AWS Shared Responsibility Model ➪ […]
Read More
AWS Solution Architect Interview Questions and Answers in 2021
Are you looking for some Solutions Architect Sample Questions to practice for your Interview Here is the list of AWS Solutions Architect Interview Questions that are best for AWS Solution Architect ➪ An AWS Solution Architect aspirant should get deep knowledge and experience with core cloud architecture concepts. Top Interview Questions will help them garnish their skill before any Interview. […]
Read More
[Recap] AWS Solutions Architect Associate | Training Day 4 | Object Storage Options
AWS is the leading cloud platform that provides its solutions to the top companies. With more demand in AWS cloud, the need for AWS Solutions Architect is increasing. AWS Solutions Architect is a person who is involved in designing and implementing solutions that run on Amazon cloud. Responsibilities ➽ Advising stakeholders and translating business requirements […]
Read More
Day 9: Application & Messaging Services [AWS Solution Architect Associate] [SAA-C02]
🡆SES is a highly scalable and cost-effective platform for sending and receiving emails. It reduces the complexity of building an in-house email solution and installing and operating a third-party email solution. 🡆SNS is managed service of AWS which is used to deliver push messages from the application to the subscribing ends or other applications. It […]
Read More
AWS Solutions Architect | Day 3 Review and Q/A: Security Management on AWS [SAA-C02]
AWS is a cloud computing platform that offers various compute services to build, text, store data, and deploy applications. AWS Identity and Access Management (IAM) ➪ helps you manage access to AWS services and resources securely. Using IAM, you can create and manage AWS users and groups and allow specific permissions. AWS Shield ➪ is […]
Read More
Slay Imposter Syndrome for AWS Certification Exams
Have you ever doubt your capability or felt an internalized fear It is most common to students or learners before attending exams Imposter Syndrome ➽ Imposter Syndrome is the psychological pattern in which individuals doubt their skills or accomplishments and have an internalized fear of being exposed as ‘fraud.’ How can it affect you? ➽ Imposter Syndrome is not […]
Read More