Issue– User gets below error when trying to access an SSO enabled application :-
“Your Account have been disabled.Please contact the System Administrator for further assistance”
The above error reflects the user account is Locked or disabled at the ldap server (OID, AD etc) which is identity store of OAM.
Check if you user can bind the ldap server using ldapbind ($OID_ORACLE_HOME/bin) command :-
./ldapbind -h <OID_server_name> -p <OID_Port> -D “cn=<User DN in OID>” -w “<User_Password>”
Example:-
./ldapbind -h innowave12.com -p 3060 -D “cn=testuser, cn=users,dc=innowave12,dc=com” -w “welcome1”
User gets below output:-
ldap_bind: DSA is unwilling to perform
ldap_bind: additional info: Password Policy Error :9001: GSL_ACCOUNTLOCKED_EXCP : Your account is locked. Contact your OID administrator.
User account can be unlocked either
1)From ODSM by searching the user in data browser and clicking “UnlockAccount”
2) From command line- To unlock an account, set the orclpwdaccountunlock attribute to 1
2.1) Create an ldif file (like- unlock.ldif) with following entries:-
dn: cn=<username>,cn=users,dc=my_company,dc=com
changetype: modify
add: orclpwdaccountunlock
orclpwdaccountunlock: 1
2.2) Use ldapmodify command from $OID_ORACLE_HOME/bin to load this ldif file:-
ldapmodify -p port -h host -D cn=orcladmin -q -v -f unlock.ldif
You will be prompted for orcladmin user password.
Things Good to know:-
1) User accounts get lock after exceeding failed passwords attempts limit set by OID password policy as applicable on the subtree of the user dn.
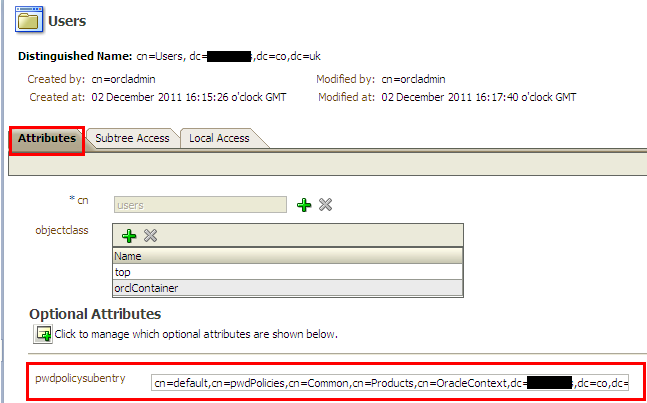
You can view the password policy applicable on user dn by selecting “pwdpolicysubentry” attribute in <user dn subtree> –> Attributes Tab –> Click optional attribute–> add “pwdpolicysubentry” and click add attribute
If the “pwdpolicysubentry” is blank , navigate to one higher subtree entry in user dn.
For example, if your user dn= “cn=testuser, cn=users,dc=innowave12,dc=com”, and you get blank value for “pwdpolicysubentry” attribute at user dn level, navigate to dn=“cn=users,dc=innowave12,dc=com” and look for value of “pwdpolicysubentry” attribute at this level.
Default OID policy is enabled in standard OID installation if not explicitly disabled.
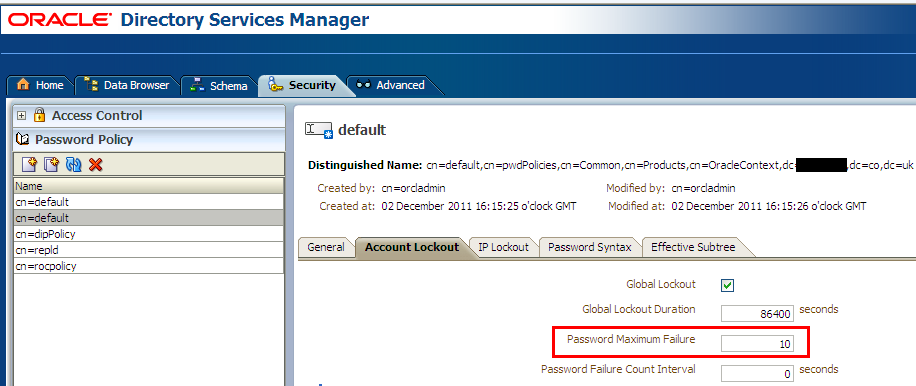
2) Under OID policy you can select the “Account Lockout” tab to see that value “Password MaximumFailure” value which signifies the number of password login attempts user can make before the password gets locked.
3) The number of failed password attempts is seen in the ‘pwdfailuretime‘ OID attibute for user entries.
You can see the failure attempts made by user by querying for “pwdfailuretime” and “pwdaccountlockedtime” for monitoring purpose:-
ldapsearch -h <OID host> -p <OID port> -D cn=orcladmin -w <orcladmin password> -b “<DN of the user>” -s base “objectclass=*” pwdfailuretime pwdaccountlockedtime
For example:-
./ldapbind -h innowave12.com -p 3060 -D cn=orcladmin -w <orcladmin password> -b “cn=testuser, cn=users,dc=innowave12,dc=com” -s base “objectclass=*” pwdfailuretime pwdaccountlockedtime
Output returns as:-
cn=testuser, cn=users,dc=innowave12,dc=com
pwdfailuretime=
20120302112534z
20120302112547z
20120302115429z
20120302115433z
20120302130044z
20120302132212z
20120302132232z
20120302145618z
20120302145629z
20120302145702z
20120305092021z
pwdaccountlockedtime=20120305092021z
Which clearly show that after 10 failed attempts user account was locked on the 11th attempt.
The pwdfailure and pwdaccountlockedtime attributes will not be returned by subsequent ldapsearch.
References:-
Oracle® Fusion Middleware Administrator’s Guide for Oracle Internet Directory
Part Number E10029-03


Comments are closed.