Category Archives for Kubernetes Security

𝐓𝐨𝐩 𝐎𝐩𝐞𝐧 𝐒𝐨𝐮𝐫𝐜𝐞 𝐊𝐮𝐛𝐞𝐫𝐧𝐞𝐭𝐞𝐬 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐓𝐨𝐨𝐥𝐬
📌 𝐊𝐮𝐛𝐞𝐫𝐧𝐞𝐭𝐞𝐬 is the most used platform among admins and developers. Containerization has made it easier than ever to swiftly design and deploy application environments with Kubernetes. However, security is the most common source of concern when it comes to container adoption. 📌 𝐊𝐮𝐛𝐞𝐫𝐧𝐞𝐭𝐞𝐬 security is all about establishing and implementing security measures to protect […]
Read More
𝐃𝐚𝐲 4 𝐑𝐞𝐯𝐢𝐞𝐰 𝐚𝐧𝐝 𝐐/𝐀: 𝐒𝐞𝐜𝐮𝐫𝐞 𝐈𝐧𝐠𝐫𝐞𝐬𝐬, 𝐚𝐧𝐝 𝐑𝐞𝐬𝐭𝐫𝐢𝐜𝐭 𝐀𝐜𝐜𝐞𝐬𝐬 𝐭𝐨 𝐍𝐨𝐝𝐞 𝐌𝐞𝐭𝐚𝐝𝐚𝐭𝐚 [𝐂𝐊𝐒]
📌 𝐔𝐩𝐠𝐫𝐚𝐝𝐞 𝐊𝐮𝐛𝐞𝐫𝐧𝐞𝐭𝐞𝐬 𝐂𝐥𝐮𝐬𝐭𝐞𝐫 ➪ Software aging is the most obvious reason for a Kubernetes upgrade. We are required to upgrade the cluster to keep up with the latest security features and bug fixes, as well as benefit from new features being released on an on-going basis. 📌 𝐊𝐮𝐛𝐞𝐫𝐧𝐞𝐭𝐞𝐬 𝐬𝐞𝐜𝐫𝐞𝐭𝐬 ➪ Secrets are used to […]
Read More
[Recap] Day 2 [CKS]: Kubernetes RBAC, Service Account and Network Policy [Certified Kubernetes Security Specialist]
certified Kubernetes Security Specialist | Day 2 Review and Q/A: Kubernetes RBAC, Service Account and Network Policy [Certified Kubernetes Security Specialist]Role-based access control (RBAC) ➪ is a way of regulating access to Kubernetes object resources based on certain roles of individual users within any organization.Service accounts ➪ are used to provide an identity to the […]
Read More
[Recap] Day 1: Kubernetes Components, Architecture, and Installation [Certified Kubernetes Security Specialist] [CKS]
Certified Kubernetes Security Specialist | Day 1 Review and Q/A: Kubernetes Components, Architecture, and Installation [Certified Kubernetes Security Specialist] [CKS] Kubernetes Security ➪ uses an approach to divide the security strategies applied in Cloud-native systems into four different layers known as 4Cs of Cloud-native Security. These 4Cs are as follow: • Code • Container • […]
Read More
Container Image Security: An Overview, Best practices, Image Scanning Tools
What is a Container? Containers, in simple terms, are the objects that package your application and its dependencies and help you run them anywhere you want! What is a Container Image? A container image is a lightweight, standalone, executable package of software that includes everything needed to run an application: code, runtime, system tools, system […]
Read More
Secure and Harden Kubernetes, AKS and EKS Cluster with kube-bench, kube-hunter and CIS Benchmarks
🛡️Security is a concern that never fades away! And Kubernetes is no exception. ☸️ Is security a concern in Kubernetes? Well, yes and no. No, because it doesn’t come with the most secure environment by default. Yes, since configuring or clusters with the CIS Benchmarks and 3-party tools can be hardened and secured. ✅ What […]
Read More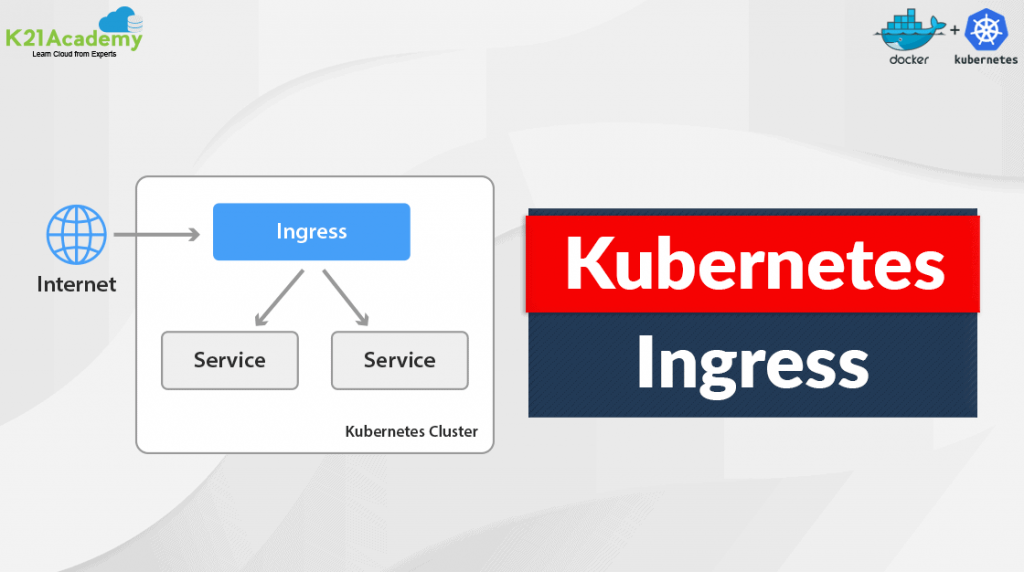
Secure Kubernetes with Ingress
We can write our own routing rules, which are implemented in seconds, and these rules also can be utilized in the application source code. Furthermore, endpoints like REST-APIs, static content, and dynamic web front ends may all be accessed via one IP address, potentially serving content for multiple domain names. This is often precisely what […]
Read More
Docker Image Vulnerabilities & Trivy Image Scanning Demo
Docker containers in today’s world is seeming to be a must for application deployment! A docker image is a file that defines which data and processes should exist inside a particular container when it starts. Any docker image be it from official repositories or the one built on your own might have vulnerabilities and possess […]
Read More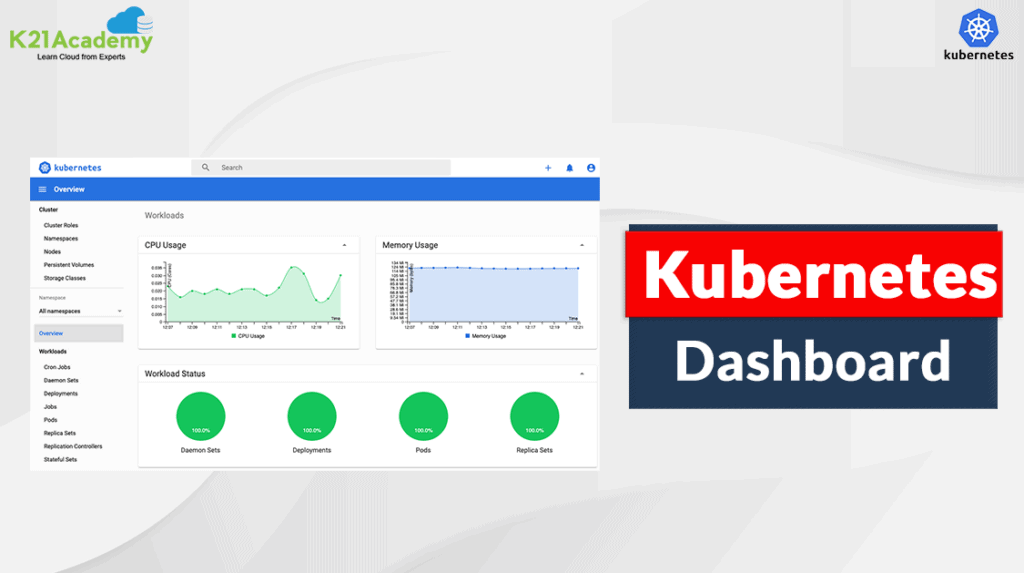
Kubernetes Dashboard: An Overview, Installation, and Accessing
Most of us love the GUI based interactions rather than the old and boring CLI ones. Are you wondering if the K8s also has a GUI which makes our lives a lot easier? Yes, it does! Its called the Kubernetes Dashboard. The web-based console, which is a general-purpose UI made to look after the Cluster […]
Read More
Kubernetes Installation Options: The Hard Way, Kubedm, MiniKube, Managed K8s (EKS, AKS, OKE, GKE)
When you install Kubernetes, choose an installation type based on ease of maintenance, security, control, available resources, and expertise required to operate and manage a cluster. You can deploy a Kubernetes cluster on a local machine, cloud, or choose a managed Kubernetes cluster. If you are interested in Docker & Kubernetes and wish to know […]
Read More