This is part II of SSL in WebLogic Server that covers creating KeyStore, generating Certificate Signing Request (CSR), importing Certificate in KeyStore, and finally using this keyStore with WebLogic Server. I strongly recommend to go through Part I “SSL in WebLogic KeyStore, Identity & Trust Store, Root and Intermediate CA“
High Level Steps to configure SSL in WebLogic Server are
1. Create Java KeyStore (JKS) and generate key
2. Generate Certificate Signing Request (CSR)
3. Send this certificate request file to CA to issue certificate
4. Import Root CAs certificate
5. Import intermediate CAs certificate (If any)
6. Import certificate issued by CA
7. List content of keystore
8. Configure SSL in WebLogic Server
—8.1 Change KeyStore type in WebLogic Server
—8.2 Specify path of Identity KeyStore and Trust KeyStore
—8.3 Specify Private Key Alias in WebLogic Server
—8.4 Enable SSL in WebLogic Server
9. Test SSL in WebLogic Server
Low Level Steps to configure SSL in WebLogic Server
1. Create Java KeyStore and generate key: First step is to create KeyStore and private key (If you already have a keyStore then you can use that to generate key)
keytool -genkey -alias myAlias -keyalg RSA -keysize 2048 -dname “CN=serverName, OU=MyOrganizationUnit, O=myOrganization,L=myLocation, ST=myState, C=myCountry” -keypass [privat_key_password] -keystore [keystore_name].jks -storepass [keystore_password]
____
[aiam@innowave21 ~]$ keytool -genkey -alias innowave21 -keyalg RSA -keysize 2048 -dname “CN=innowave21.focusthread.com, OU=DBATeam, O=onlineAppsDBA, L=London, ST=London,C=GB” -keypass welcome1 -keystore innowave21.jks -storepass welcome1
[aiam@innowave21 ~]$ ls *.jks
innowave21.jks
_____
Note:
a) This step will create Keystore [keystore_name].jks
b) keytool utility is a Key and Certificate Management Tool and is available in $JAVA_HOME/bin
c) -genkey option signifies that we are generating private keys
d) -alias myAlias : Each entry in KeyStore (JKS) is represented by Alias. When you import signed certificate (issued by CA) in KeyStore then you should use same alias (used during key generation)
e) -keyalg RSA : is algorithm used to generate keyPair (default algorithm is DSA)
f) -keysize 2048 : is size of key used to generate private key
g) -dname : represents name of server to which certificate key is created. If you are generating keys for server innowave21.focusthread.com then use CN=innowave21.focusthread.com, OU=………
2. Generate Certificate Signing Request: Next step it so generate Certificate Signing Request (CSR) for Key (with alias innowave21) generated in previous step
keytool -certreq -alias myAlias -keystore [keystore_name].jks -storepass [keystore_password] -file [certificate_request].csr
_____
keytool -certreq -alias innowave21 -keystore innowave21.jks -storepass welcome1 -file innowave21.csr
[aiam@innowave21 ~]$ ls *csr
innowave21.csr
_____
a) This step will create certificate signing request file
b) -certreq signifies that we are generating certificate signing request file
c) -alias myAlias must be same as one used during key generation in previous step
3. Send this certificate request file to Certifying Authority (CA) to issue certificate
4. Import Root CA certificate.
Once you receive certificate for your server then you must import certificate of Authority issued the certificate (before importing certificate issued by CA)
keytool -import -trustcacerts -alias rootcacert -keystore [keystore_name].jks -file rootCA.cer -storepass [keyStorePassword]
a) This step will import certificate of Certifying Authority (CA) with alias as rootcacert in KeyStore
b) -import signifies that we are importing certificate in keystore
c) -trustcacerts signifies that we are importing trusted certificates (In this case KeyStore is acting as trust Store, remember trust store and identity store discussed in part I ??). If you don’t use option -trustcacerts then it will try to import certificate as Identity Certificate
d) -alias must be different from one used during key generation
e) -file rootCA.cer is file that contains certificate of Root Certifying Authority (remember Root and Intermediate Certifying Authority discussed in part I ?? )
5. Import intermediate CA (If Any) certificate
If there are more than one Certifying Authority (CA) then you must import any intermediate CA
keytool -import -trustcacerts -alias intermediatecacert -keystore [keystore_name].jks -file intermediateCA.cer -storepass [keyStorePassword]
a) -import signifies that we are importing certificate in keystore
b) -trustcacerts signifies that we are importing trusted certificates (In this case KeyStore is acting as trust Store, remember trust store and identity store discussed in part I ??). If you don’t use option -trustcacerts then it will try to import certificate as Identity Certificate
c) -alias must be different from one used during key generation or while importing root CA
d) -file intermediateCA.cer is file that contains certificate of Intermediate Certifying Authority
6. Import Server Certifucate
Next step is to import Server Certifictae
keytool -import -alias myAlias -keystore [keystore_name].jks -file servercert.cer -keypass [keyPassword] -storepass [keyStorePassword]
a) -import signifies that we are importing certificate in keystore
b) -alias myAlias should match with Alias used during generation of Key
c) -file servercert.cer is file that contains certificate of server issue by CA
If you want to view certificate stored in KeyStore then you can use option -list like below
keytool -list -v -keystore [keystore_name].jks -storepass [keyStorePassword]
8. Configure SSL in WebLogic Server
In steps above Trust Store (store containing Root and Intermediate CA) and Identity Store (store containing Server Certificate) are same i.e. [keystore_name].jks .
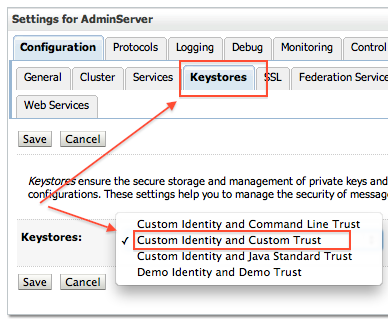
8.1 Change KeyStore type from “Demo Identity and Demo Trust” to “Custom Identity and Custom Trust”
WebLogic Server Console -> Name of Server (for which you wish to configure SSL) -> Configuration -> KeyStores -> change (next to Key Stores)
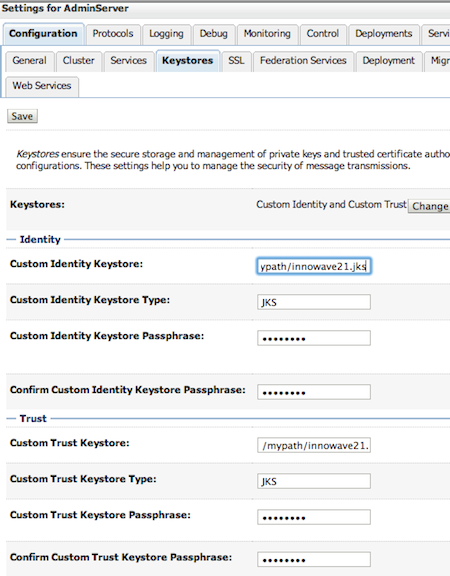
8.2 Specify path of Identity KeyStore and Trust KeyStore
In steps above Trust Store (store containing Root and Intermediate CA) and Identity Store (store containing server certificate) are same i.e. [keystore_name].jks (innowave21.jks in my case).
- Specify passphrase as password used for KeyStore
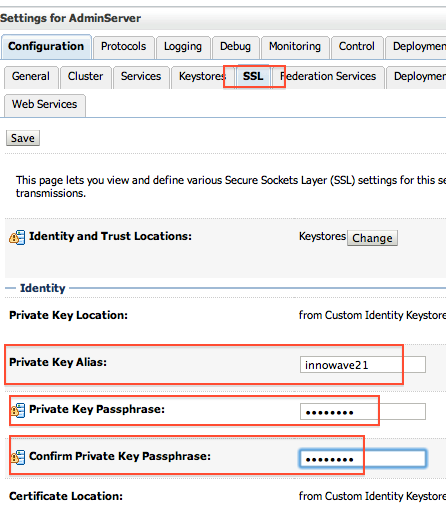
8.3 Specify Private Key Alias in WebLogic Server
Enter the Alias you used during creation of certificate request and password of KeyStore
WebLogic Server Console -> Name of Server (for which you wish to configure SSL) -> Configuration -> SSL
8.4 Enable SSL in WebLogic Server
Finally enable SSL in WebLogic Server ; WebLogic Server Console -> Name of Server (for which you wish to configure SSL) -> Configuration -> General
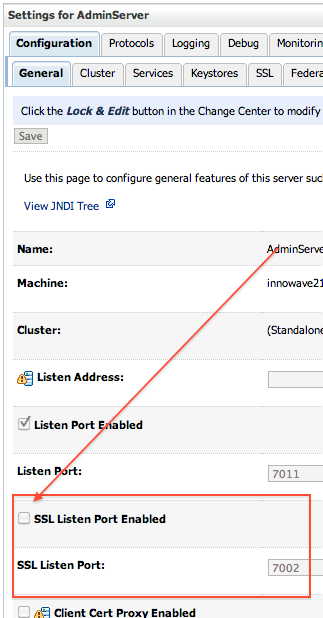
9. Test SSL in WebLogic Server
https://:
References
- Keytool – Key and Certificate Management Tool
- Configure SSL in WebLogic Server
- My Oracle Support Note : 1230333.1 How to Create a Java Keystore via Keytool in FMW 11g
- Configure Key Store
Did you get a chance to download Free Interview Questions related to WebLogic? If not, download it here http://k21academy.com/weblogic-interview-question
Learn Oracle Weblogic Server Administration
If you want to learn Oracle WebLogic Server Administration with tons of additional features like Live Interactive Sessions, Life time access to membership portal, Free re-taking sessions for next one year, Dedicated Machine to practice, On Job Support and much more


Comments are closed.