.
Password Policy in Oracle Access Manager’s Password Management Services(available in OAM’s Identity System) enable you to define multiple password policies, constraints on password composition, forced-password change and lost password management feature.
.
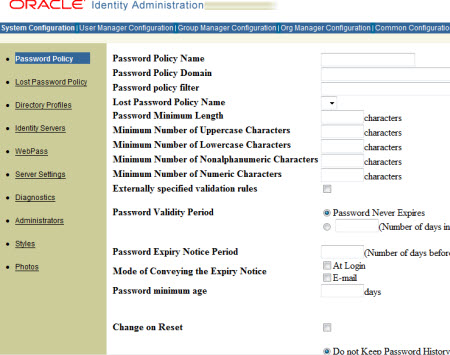
Password Policy : is set of rules that governs kind of passwords that users create and validity of password (duration)
.
.
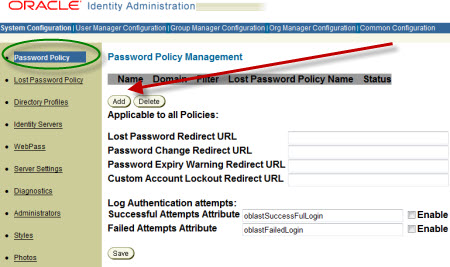
- You configure Password Policy from Identity System Console -> System Configuration -> Password Policy
- Password Policies are created in Identity System (OAM consists of two parts Identity System and Access System) but also applicable to access system. These policies also apply to users who try to access resources protected by Access System
- You can create multiple password policiesapplicable at different level in your domain (or realm) for example if your domain (in LDAP server) DC=com, DC=onlineappsdba, OU=EMEA, OU=UK, cn=user1 then you can have multiple password policies applicable at different level i.e. policy1 (applicable at DC=onlineappsdba), policy2 (applicable at OU=EMEA), policy3(applicable at OU=UK) and policy4 (applicable at cn=user1)
- Password Policies are evaluated at bottom-to-top level, i.e. if you have password policy at user level then that password policy will be applicable. If not then it will check for password policy applicale at OU=UK. If there is no password policy at OU=UK level then it will look for password policy applicable to OU or DC levelhigher to that.
- There are three type of administrator users in OAM
a) Master Administrators : They have administrative access to both Identity and Access System
b) Identity Administrators : They have administrative access to Identity System)
c) Access Administrators (They have administrative access to Access System)
Only Master Administrators have access to configure password policies in Oracle Access Manager.
- If you have password policy where change on reset is enabled (user must change password after password reset) but NO Password Change Redirect URL is defined, This prevents users from changing password and ultimately logging in
- Directory Server (OID, AD…) may have its own password Policy, Password Policy on Directory Server should not be more strict than Access Manager Password Policy otherwise it will create conflicts. For Example if Password Policy in OAM dictates that OAM should lock account after 5 continuous failed login attempts where as in Directory Server (AD, OID..) account lockout policy is 3 attempts then it will conflict with OAM’s Password Policy
- You can create default password policy that apply to all domains. You can create Password Policy to specific directory domain or Multiple policies with in domain
- Object Class for Password Policy in Oracle Access Manager is OblixPersonPasswordPolicy
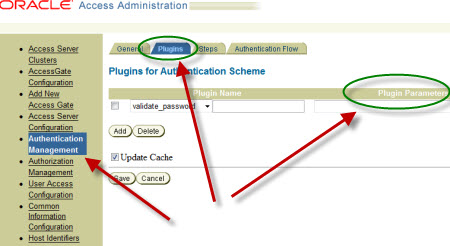
- To implement password policy in OAM, define Password Policy using Identity System Console and then modify Authentication Scheme in Access System (add obReadPasswdMode=”LDAP”, obWritePasswdMode=”LDAP” to validate_password plug-in)
.
How often Access Server checks for changes for Password Policies ?
Password Policy Reload Period (in Seconds) is access server setting which determines frequency in which Access Server checks Identity Server for new Password Policy.
Password Policies are cached in Access Server, You can manually flush Password Policy Cache in Access Server or Restart Access Server which will automatically flush Password Policy Cache.
.
How to flush password policy cache in Access Server ?
Access System Configuration -> Common Information Configuration -> Flush Password Policy
.
Reference



