Oracle Internet Directory (OID) by default listens on two ports LDAP (non secure) and LDAPS (secure LDAP), In this post I am going to cover in detail how to configure SSL in OID 11g and key points related to SSL in OID.
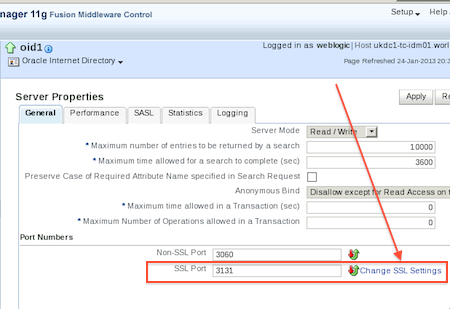
1. OID listens on two ports (LDAP and LDAPS) and list of port used is displayed by opmnctl status -l (In example below, OID is listening on SSL port 3131)
[aiam@innowave21 ~]$ opmnctl status -l
Processes in Instance: asinst_1
———————————+——————–+———+——-
ias-component | process-type | pid | status | uid | memused | uptime | ports
———————————+——————–+———+——-
oid1 | oidldapd | 26253 | Alive | 412548771 | 662564 | 371:51:57 | N/A
oid1 | oidldapd | 26213 | Alive | 412548770 | 374372 | 371:51:58 | N/A
oid1 | oidmon | 26145 | Alive | 412548769 | 298736 | 371:52:02 | LDAPS:3131,LDAP:3060
EMAGENT | EMAGENT | 26144 | Alive | 412548768 | 63824 | 371:52:02 | N/A
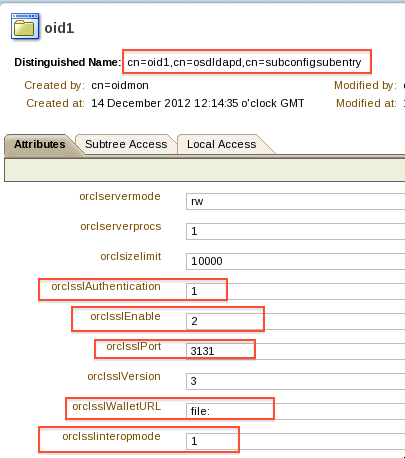
2. OID on LDAPS (secure) port can be configured in one of three modes (controlled by attribute orclSSLAuthentication)
a) SSL with No Authentication (orclSSLAuthentication = 1) – In this mode neither client (making connection to OID) nor Server (OID) presents SSL certificate . Data is transferred on SSL
b) SSL with Server Authentication Only (orclSSLAuthentication = 32) – In this mode Server (OID) presents its SSL certificate to client (making connection to OID) but client doesn’t present any certificate to Server . Data is transferred on SSL
c) SSL with Client and Server Authentication (orclSSLAuthentication = 64) – In this mode both Server (OID) and client (making connection to OID) presents their SSL certificate to each other. Data is transferred on SSL
Note: Default setting is SSL with No Authentication i.e. orclSSLAuthentication value 1. Common practice is to change this to SSL with Server Authentication Only i.e. orclSSLAuthentication = 32
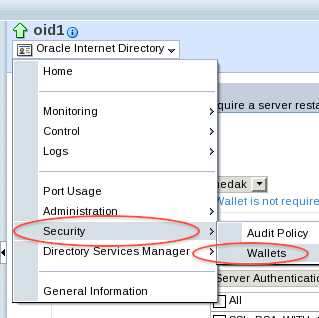
3. When OID is configured in Server Authentication (orclSSLAuthentication = 32) or (orclSSLAuthentication = 64) then SSL certificate and Certifying Authority’s (CA) certificates are stored in WALLETS (More on wallets here and here). Wallet can be managed by EM (Enterprise Manager) or WLST or orapki or OWM
Note: To manage wallets in OID 11g using EM or WLST, OID must be integrated with WebLogic with Enterprise Manager (EM).
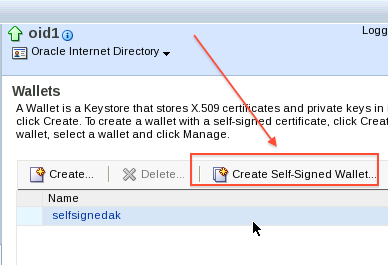
4. For SSL certificated of OID, you can generate self signed certificates or create certificate request file and submit to Certifying Authority like verisign and store certificates in wallet.
.
To configure SSL in OID
1. Configure Wallet to store SSL certificate and Certifying Authority’s certificates using EM or WLST or OWM or orapki
2. Create Certificate Request File -> Get Certificate from Certifying Authority (CA) -> Import certificate in Wallet
or
2. Generate Self Signed Certificate in Wallet
3. Configure SSL parameter using EM or WLST or update SSL related attributes for OID instance (orclSSLAuthentication, orclSSLVersion, orclSSLWalletURL)
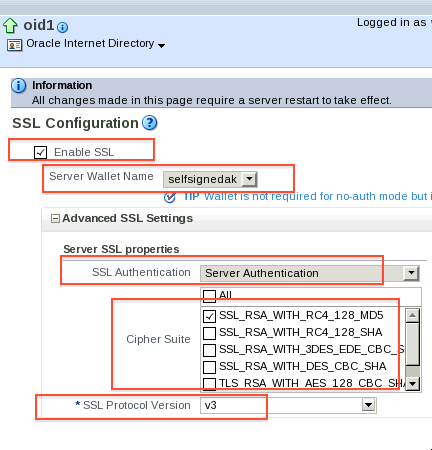
a) Ensure that Enable SSL is checked
b) Select Wallet from drop down (list will be based on wallets created in previous step – You can have more than one wallet but only one wallet will be used)
c) Select SSL Authentication Mode (orclSSLAuthentication 1 or 32 or 64)
d) Select ciphers (it is recommended to select ciphers based on enterprise security requirements)
e) Select SSL version (version 3 is recommended)
4. Restart OID using opmnctl stopall; opmnctl startall
5. Test SSL connection from ldapbind or ODSM or using LDAP browser
Here is OID instance configuration after configuring SSL
More on OID SSL configuration in OID Administrators Guide
FREE Webinar on
Oracle Fusion Middleware Concepts / SSL
Webinar with Oracle ACE Atul Kumar on Oracle Fusion Middleware Concepts like Java VS System Component, SSL
Click here to register FREE Live Webinar


Comments are closed.