Readers,
It’s been sometime since writing here, however I believe I am back with good informative post today. It is very common ask for MFA these days and there are multiple ways to achieve this in Oracle Access Management by using either OAM 11g or combination of OAM and OAAM 11g (and/or using 3rd party products). The latter is enriched with fraud detection challenging with questions and/or SMS/OTP etc., whereas former is based on OTP or push notification.
I am going to cover latter part by using Oracle Access Manager 11g alone. Oracle Access Manager 11g supports various types of MFA possibilities, here they are:
- Oracle Mobile Authenticator (OTP)
- SMS/Email Notification (OTP)
- Push notification from Oracle Mobile Authenticator
Oracle Mobile Authenticator app is available on Andriod and iOS. The standard mechanism to implement TOTP (time based OTP) is using TOTPPlugin. TOTPPlugin is pre-packaged with OAM 11g product, so usually no additional component development is needed. The second mechanism to implement TOTP is using AdaptiveAuthentication Plugin which is also pre-packaged with OAM 11g product.
If you for any reason you are having challenge with OTP working with TOTP plugin, you can use Adaptive Authentication plugin which is my case :).
I will cover AdaptiveAuthentication Plugin implementation in this post while others are topic for another day.
I would assume that you have configured Oracle Mobile Authenticator already. Follow the steps below to implement MFA using Adaptive Authentication Plugin.
- Login to OAM Admin console as admin user.
- Goto Plugins.
- Specify the Configuration Parameters for Adaptive Authentication Plugin. More importantly Identity Store, TotpSecretKeyAttribute etc., Save the changes.
- Goto Modules.
- Open AdaptiveAuthentication Module.
- Goto Steps and specify the configuration parameters for SecondFactorOTP step.
- Verify that AdaptiveAuthenticationScheme is properly configured for configuration parameters.
- Specify the step up authentication scheme in post-authentication of Advanced Rules in authentication policy.
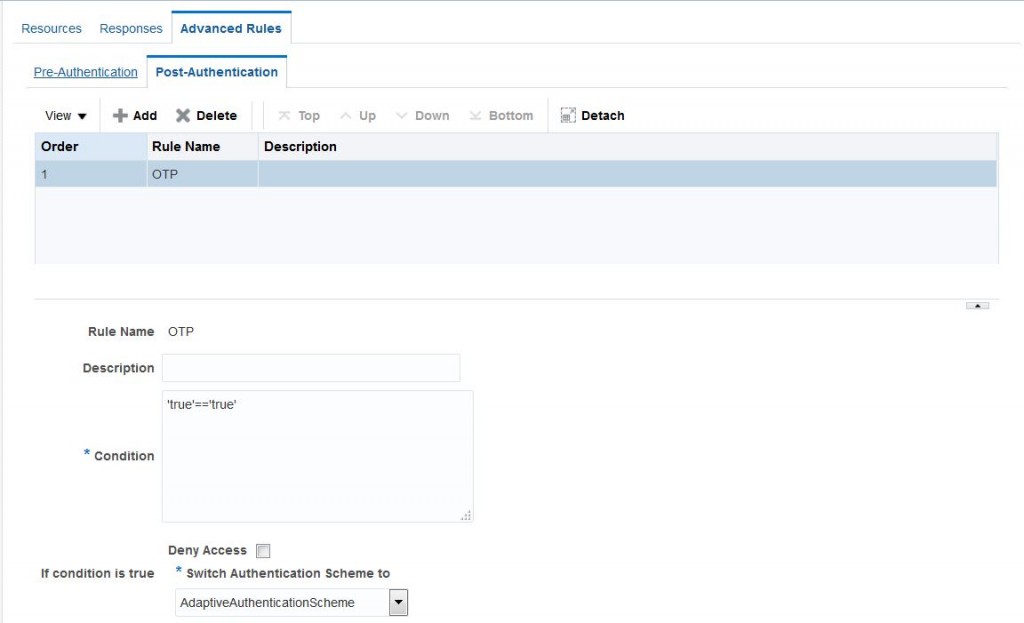
That’s it, you are good to test.
Access OAM protected application and after regular user authentication (form, kerberos etc.,), user is redirected to another page to confirm preferred method for MFA as shown below.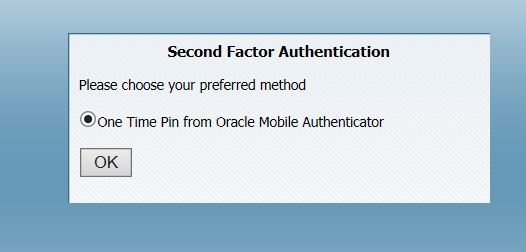
When One time Pin from Oracle Mobile Authenticator is selected, user is redirected to Second Factor Authentication Page as shown below. 
User should enter OTP code generated in mobile authenticator in this page and user will be redirected to requested application.
References:
https://docs.oracle.com/cd/E52734_01/oam/AIAAG/adaptive_auth_intro.htm#AIAAG89731


Comments are closed.