Leave a Comment:
21 comments
Hi Atul,
I have integrated OAM and OAAM 11gR2 but I do not see an option for change password at 1st time login. Point ii b) that you have mentioned above. Do we need to do anything extra to have that implemented ?
Reply[…] When you integrate OIM/OAM/OAAM (using Advanced Integration via TAP) more information here , username/password is collected by Oracle Adaptive Access Manager (OAAM) and then OAAM passes […]
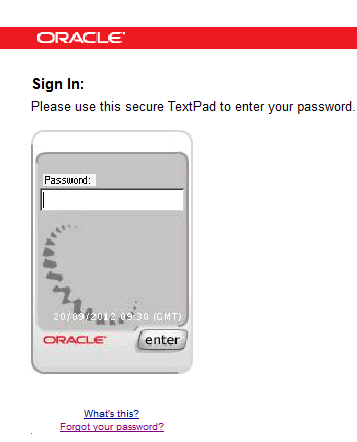
ReplyI meant to say that for unregistered users login for first time, I do not get an option to reset the password. I just get a imageless textpad for password (which is expected), then takes me to the Registration Page for Images and phrases and from there to the application.
I do not get an option to reset the password.
Reply[…] 7. You can integrate OIM with OAAM for challenge questions so that OAAM is used as setting/validation of Challenge Questions . More on OIM-OAAM integration here and on request flow for OIM-OAM-OAAM integration here […]
ReplyThanks Atul but it doesnt solve my query. I have OIM-OAM and OAAM integrated. I create a user in OIM and provide him access to app1. The user logs into app1 and gets a OAAM login page. he enters his uid, gets a generic blank textpad. he enters his password. He gets an option to register questions as he is a new user and once done its redirected back to the app page. I do not get an option to change the password at first login instead of haveing the pwd policy in OID enabled with the attribute “Reset Password upon Next Login” enabled
ReplyHi Atul,
Thanks for the blog. It is really helpful.
I need one help on OIM-OAM-OAAM integration.
I am done with integration, Now i want to reset the security question in OAAM.
I have configured urls for Reset question in OIM and oaam as in document.
But when i try to hit the link http://host:port/oaam_server/oimResetChallengeQuestions.jsp
I will redirected to OAAM TAP scheme login Page
After Succeful authentication, I can See OAAM authentication page (not TAP scheme) instead of Reset challenge question page
@ Harpreet,
Let me clear on reset password – Do you mean
a) Forgot password (user has not logged in yet)
or
b) Change Password (user has logged in to system OIM and would like to change password)
Which one would you like to do ?
Reply@ Nash,
Change password on next logon – when integareted with OIM-OAM is controlled by OAM . There is an attribute ob****** that says that user must change password on next login.
Please confirm if OIM is also configured and user is created via OIM .
If yes then share verison of OIM.
Reply@atul
I am doing Reset challenge question.
I know the direct URL of reset security question:
http://host:port/oaam_server/oimResetChallengeQuestions.jsp
but It does not work directly.
I know it works fine from OIM delegation admin page.
I wanted help on if there are any webservices that can be utilized. as i want to make this happen from my portal not from OIM console
@ Harpreet,
Yes, this may not work from external portal. Check with Oracle Support and see what is this URL doing when accessed from with in OIM portal.
Thanks Atul,
Yes I have OIM,OAM and OAAM all 11g R2 integrated with OID 11.1.1.6
ReplyHi Atul,
Here you are using all components of same version i.e. 11gR2, but can OIM 11gR1 be integrated with OAM 11gR2 ?
@ Deepika,
What components from 11gR1 and which component fro 11gR2 you wish to integarte ?
Hi Atul,
Things are bit changed now.
The current scenario is that we have already installed OIM 11gR1 in our environment, and we need to install OAM 11gR2 in same environment.
So I want to know that is there any necessity to upgrade OIM to R2 or can we install OAM in a different weblogic domain( I hope installing in different domain will not give any OIM-OAM version conflict issue)?
@ Deepika,
This is one of those difficult ones to answer, I am not sure what is Oracle’s standpoint on this (If you ask for production they might say NO this is not supported)
This solution (OIM 11gR1 and OAM11gr2) technically should work but suggestion would be to do end to end testing .
Why don’t you install OAM 11gR1 only what is business justification for OAM 11gR2 when OIM is 11G R1 .
Ideal world is to upgrade OIM to 11gR2 and integrate with OAM 11gR2
Atul Kumar
Reply[…] can find Atul’s post here. Filed Under: Identity Management jQuery(document).ready(function(){ […]
ReplyDoes advanced with TAP OAAM-OAM integration work in simple mode. We have a working integrationw ith 11g webgates in open mode but after changing the mode to simple, we keep getting ssl handshake error.
ReplyAnother question that I have, Is it possible to use the forgot password/change password feature when only OAM-OAAM are integrated. We dont use OIM and when we try to type in the new password in the forgot password flow, ldap call is not made to update the password in ldap.
Is it possible to use forgot password without OIM?
ReplyHi Atul,
Any response to the above questions? Have you implemented this before?
ReplyCan I use the multifactor authantication of OAAM with the partners (federated resources) in Identity Provider Administration tab in OAM ? as Personalized Image&message or Challenge Questions
ReplyChange password on next logon – when integareted with OIM-OAM is controlled by OAM . There is an attribute ob****** that says that user must change password on next login.
Please confirm if OIM is also configured and user is created via OIM .
If yes then share verison of OIM.
Reply