A well written post by Andre Correa on Fusion Middleware Security Blog says “One of the main strengths of SAML is the ability to communicate identity information across security domains that do not necessarily share the same user base. In other words, the authenticated user in one security domain does not necessarily exist in the target security domain providing the service.”
This concept where user authenticated in one domain doesn’t exist in another domain but trusted by second domain (as part of SAML assertion) is called as Virtual User. This post covers covers how to set this virtual user in Oracle Web Services Manager (OWSM) that is used to protect WebServices deployed on SOA/ OSB.
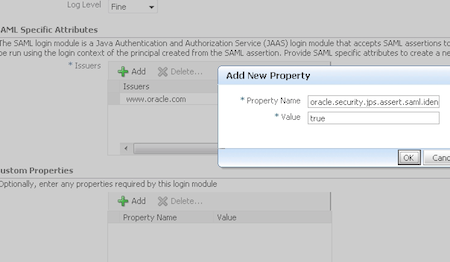
OWSM delegated authentication of incoming subject in SAML assertion to Oracle Platform Security Services (OPSS). OWSM uses SAML Login Module (saml.loginmodule or saml2.loginmodule ) and to enable virtual user in OWSM you set property oracle.security.jps.assert.saml.identity=true in jps-config.xml located at $DOMAIN_HOME/config/fmwconfig )
Property oracle.security.jps.assert.saml.identity is a domain-wide property used to determine the mapping between the SAML subject and the user.
Valid values include:
a) false—When this flag is set to false, the username in the SAML subject is mapped to the actual user in the identity store. The user roles and subject are created with username and roles specified in the identity store. This is the default value.
b) true—When this flag is set to true, the SAML subject is treated as a logical/virtual user. The user is not mapped to the actual user in the identity store. The subject is populated only with the username from the SAML subject. Because the subject is treated as a virtual user, identity store configuration is not required and the Identity Assertion Provider is not invoked for all SAML policies in the domain using this login module.
To set Virtual User (aka logical user)
1. Login to Enterprise Manager of WebLogic domain and go to WebLogic Domain
2. From WebLogic Domain drop down menu, Security -> Security Provider Configuration -> Login Modules -> Edit
3. Add custom property oracle.security.jps.assert.saml.identity=true
4. Restart Admin and managed servers in WebLogic Domain
Related/References

Comments are closed.